Remote Access
Real-Time Interaction, Direct Resolution

Remote Commands
Instant Actions, Total Control
Lock/Unlock
Lock devices suspected of
being lost or stolen to prevent
unauthorized use.
being lost or stolen to prevent
unauthorized use.
Factory Reset
Restore devices to their factory
settings to resolve critical issues or
securely repurpose hardware.
settings to resolve critical issues or
securely repurpose hardware.
Shutdown/Restart
Power off or reboot devices
remotely to apply changes, resolve
issues, or perform maintenance.
remotely to apply changes, resolve
issues, or perform maintenance.
Clear Screen Lock Password
Remove forgotten or misconfigured
screen lock passwords to restore access
without data loss.
screen lock passwords to restore access
without data loss.
Remote Debugging
Advanced Diagnostics, Faster Solutions
Log Retrieval for Troubleshooting
Remotely collect device logs for in-depth diagnostics and faster issue resolution. This eliminates the need to physically access the device to get the information needed to solve a problem.

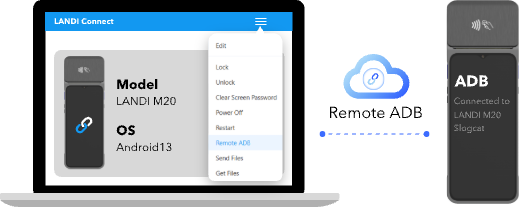
Remote ADB (Android Debug Bridge)
Enable secure ADB sessions over the air for advanced remote debugging and command execution. This powerful tool gives technical teams the ability to investigate and solve problems efficiently.
Benefits of Remote Assistance
Enhanced
Operational Efficiency
Operational Efficiency
Empowers teams with
powerful tools to provide
support remotely.
powerful tools to provide
support remotely.

Minimized
Downtime
Downtime
Eliminates the travel
and shortens the
turn-around time.
and shortens the
turn-around time.

Reduced
Costs
Costs
Reduces costs by
removing the need for
physical travel to device
locations.
removing the need for
physical travel to device
locations.

Faster Response
Time
Time
Start the troubleshooting
immediately with remote
access to the device.
immediately with remote
access to the device.

Improved
Security
Security
Lock devices remotely or
reset them to factory setting
to prevent authorized use
or data leaks.
reset them to factory setting
to prevent authorized use
or data leaks.

Remote Access
Real-Time Interaction,
Direct Resolution

Remote Commands
Instant Actions, Total Control
Lock/Unlock
Lock devices suspected of
being lost or stolen to prevent
unauthorized use.
being lost or stolen to prevent
unauthorized use.
Factory Reset
Restore devices to their factory
settings to resolve critical issues or
securely repurpose hardware.
settings to resolve critical issues or
securely repurpose hardware.
Shutdown/Restart
Power off or reboot devices remotely
to apply changes, resolve issues, or
perform maintenance.
to apply changes, resolve issues, or
perform maintenance.
Clear Screen
Lock Password
Remove forgotten or misconfigured
screen lock passwords to restore
access without data loss.
screen lock passwords to restore
access without data loss.
Remote Debugging
Advanced Diagnostics,
Faster Solutions

Log Retrieval for Troubleshooting
Remotely collect device logs for in-depth diagnostics and faster issue resolution. This eliminates the need to physically access the device to get the information needed to solve a problem.
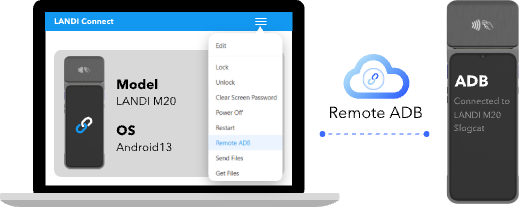
Remote ADB (Android Debug Bridge)
Enable secure ADB sessions over the air for advanced remote debugging and command execution. This powerful tool gives technical teams the ability to investigate and solve problems efficiently.
Benefits of Remote
Assistance
Enhanced
Operational
Efficiency
Operational
Efficiency
Empowers teams with
powerful tools to provide
support remotely.
powerful tools to provide
support remotely.

Minimized
Downtime
Downtime
Eliminates the travel
and shortens the
turn-around time.
and shortens the
turn-around time.

Reduced
Costs
Costs
Reduces costs by
removing the need for
physical travel to device
locations.
removing the need for
physical travel to device
locations.

Faster Response
Time
Time
Start the troubleshooting
immediately with remote
access to the device.
immediately with remote
access to the device.

Improved
Security
Security
Lock devices remotely or reset them to
factory setting to prevent authorized use or
data leaks.
factory setting to prevent authorized use or
data leaks.









































